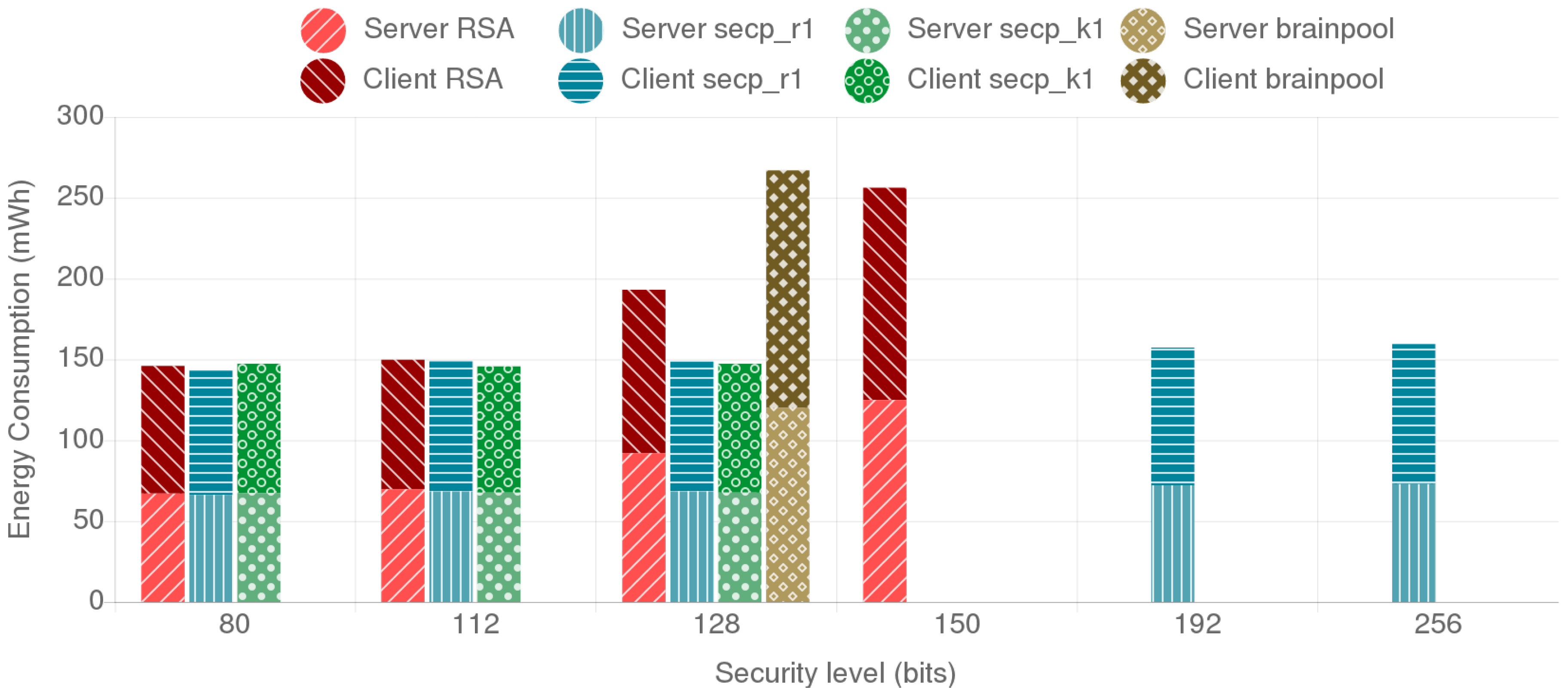
Sep 01, 2011 do not use this post to learn about aes encryption in python. I did not have sufficient experience with bytes, strings, and encryption when i wrote this. I will have a new post with python3 (and hopefully it will have better information). Jun 25, 2010 AES encryption of files in Python with PyCrypto. It expects your key to be either 16, 24 or 32 bytes long (for AES-128, AES-196 and AES-256, respectively). The longer the key, the stronger the encryption. In this case I recommend picking a password and then using the SHA-256 digest algorithm from hashlib to generate a 32-byte key from.
| fromCrypto.CipherimportAES, XOR# from pycrypto library (https://www.dlitz.net/software/pycrypto/) |
| block_size=AES.block_size |
| defdecrypt(key, ciphertext): |
| # assume: len(key) len(IV) 16 bytes; no padding |
| iv=ciphertext[:block_size] |
| ciph=ciphertext[block_size:] |
| cipher=AES.new(key) |
| ivn=int(iv.encode('hex'), 16) # the IV string in numeric form |
| plain_blocks= [] |
| i=0 |
| whileTrue: |
| ciph_block=ciph[(i*block_size):((i+1)*block_size)] |
| ifnotciph_block: # the last iteration was the last block |
| # calculate junk 'padding' length |
| last_ciph_block=ciph[((i-1)*block_size):] |
| last_ciph_block_len=len(last_ciph_block) |
| # and remove that many junk bytes from the last plain text block |
| last_plain_block=plain_blocks[-1] |
| plain_blocks[i-1] =last_plain_block[:last_ciph_block_len] |
| # then break out of this loop, we are done |
| break |
| xor=XOR.new(ciph_block) |
| # calculate the IV + i for this block in byte string |
| iv=hex(ivn+i)[2:] # add i to IV, then convert to hex (removing the '0x' prefix) |
| ifiv[-1] 'L': # remove 'L' suffix in python's hex representation string |
| iv=iv[:-1] |
| iflen(iv) <16: # prepend zeroes if the hex string is < 16 bytes |
| iv='0'* (16-len(iv)) +iv |
| iv=iv.decode('hex') # convert again the hex string into byte string |
| plain_block=xor.decrypt(cipher.encrypt(iv)) # encrypt the modified IV, then XOR with cipher block |
| i+=1 |
| plain_blocks.append(plain_block) |
| return'.join(plain_blocks) |
| if__name__'__main__': |
| keys_ciphertexts_hex= [ |
| ('36f18357be4dbd77f050515c73fcf9f2', '69dda8455c7dd4254bf353b773304eec0ec7702330098ce7f7520d1cbbb20fc388d1b0adb5054dbd7370849dbf0b88d393f252e764f1f5f7ad97ef79d59ce29f5f51eeca32eabedd9afa9329'), |
| ('36f18357be4dbd77f050515c73fcf9f2', '770b80259ec33beb2561358a9f2dc617e46218c0a53cbeca695ae45faa8952aa0e311bde9d4e01726d3184c34451'), |
| ] |
| forkey_hex, ciphertext_hexinkeys_ciphertexts_hex: |
| key=key_hex.decode('hex') |
| ciphertext=ciphertext_hex.decode('hex') |
| printrepr(decrypt(key, ciphertext)) |
Nov 03, 2016 Well, it's been bugging me all day, I report it and I've had a glass of wine and now it's just gone away. ¯(ツ)/¯ Anyway, thanks for the code sir, you're making life better 👍. Sep 26, 2019 This only works because the 'mysecretpassword' is 16 bytes. If it were a different (not dividable by 16) amount of bytes you'd get 'ValueError: AES key must be either 16, 24, or 32 bytes long'. It describes a symmetric-key algorithm using the same key for both encrypting and decrypting. AES Encryption: Encrypt and decrypt online. The Advanced Encryption Standard (AES), also known by its original name Rijndael is a specification for the encryption of electronic data. It describes a symmetric-key algorithm using the same key.
commented Jul 4, 2017
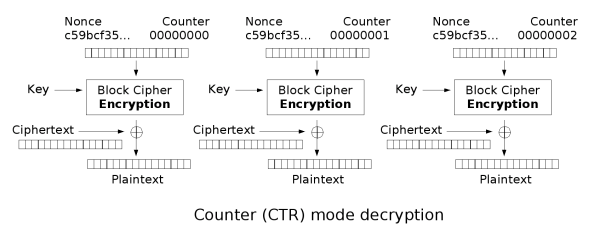
CTR mode lets you build a stream cipher from a block cipher. |