- Generate Private Key From Certificate Request Sample
- Generate Private Key From Certificate Request Form
- Generate Private Key From Certificate Request Online
- Windows Generate Certificate Request
You can also use Microsoft IIS to generate a Private Key and CSR.
How to generate a CSR in Microsoft IIS 7
Jul 08, 2009 For testing purpose, you can generate a self-signed SSL certificate that is valid for 1 year using openssl command as shown below. You can use this method to generate Apache SSL Key, CSR and CRT file in most of the Linux, Unix systems including Ubuntu, Debian, CentOS, Fedora and Red Hat. Nov 29, 2017 If you try to export a certificate from the Issued folder on the CA, you can only export (Copy To File) as a.cer file, which won’t include the private key. If you follow the steps above to export the certificate, you can still import the certificate onto the server, but in the Certificate Manager MMC, you won’t see the key icon showing. Select the private key that you wish to backup. Right click on the file and choose All Tasks Export 9. The certificate export wizard will start, please click Next to continue. In the next window select Yes, export the private key and click Next 10. Leave the default settings selected and click Next. Click Start, Control Panel, Administrative Tools, and then select Internet Information Services (IIS) Manager. Select the server where you want to generate the certificate In the left Connections menu, select the server name (host) where you want to generate the request. The private key (www.hostname.com.key) is stored locally on the server and is employed for decryption. The public key, in the form of a WildCard SSL Certificate Signing Request (certrequest.csr).
1. Click Start, then Administrative Tools, then Internet Information Services (IIS) Manager.
2. Click on the server name.
3. From the center menu, double-click the 'Server Certificates' button in the 'Security' section (it is near the bottom of the menu).
Jul 08, 2009 You can also generate self signed SSL certificate for testing purpose. In this article, let us review how to generate private key file (server.key), certificate signing request file (server.csr) and webserver certificate file (server.crt) that can be used on Apache server with modssl. Key, CSR and CRT File Naming Convention. Sep 11, 2018 You apply by generating a CSR with a key pair on your server that would, ideally, hold the SSL certificate. The CSR contains crucial organization details which the CA verifies. Generate a CSR and key pair locally on your server. The key pair consists of a public and private key.
4. Next, from the 'Actions' menu (on the right), click on 'Create Certificate Request.' This will open the Request Certificate wizard.
5. In the 'Distinguished Name Properties' window, enter the information as follows: Gta v key generator pc no survey.
- Common Name - The name through which the certificate will be accessed (usually the fully-qualified domain name, e.g., www.domain.com or mail.domain.com).
- Organization - The legally registered name of your organization/company.
- Organizational unit - The name of your department within the organization (frequently this entry will be listed as 'IT,' 'Web Security,' or is simply left blank).
- City/locality - The city in which your organization is located.
- State/province - The state in which your organization is located.
6. Click Next.
7. In the 'Cryptographic Service Provider Properties' window, leave both settings at their defaults (Microsoft RSA SChannel and 2048) and then click next.
8. Enter a filename for your CSR file.
9. Remember the filename that you choose and the location to which you save it. You will need to open this file as a text file and copy the entire body of it (including the Begin and End Certificate Request tags) into the online order process when prompted
2. Back Up Private Key
Generate Private Key From Certificate Request Sample
To backup a private key on Microsoft IIS 6.0 follow these instructions:
1. From your server, go to Start > Run and enter mmc in the text box. Click on the OK button.
2. From the Microsoft Management Console (MMC) menu bar, select Console > Add/Remove Snap-in.
3. Click on the Add button. Select Certificates from the list of snap-ins and then click on the Add button.
4. Select the Computer account option. Click on the Next button.
5. Select the Local computer (the computer this console is running on) option. Click on the Finish button.
6. Click on the Close button on the snap-in list window. Click on the OK button on the Add/Remove Snap-in window.
7. Click on Certificates from the left pane. Look for a folder called REQUEST or 'Certificate Enrollment Request> Certificates
8. Select the private key that you wish to backup. Right click on the file and choose > All Tasks > Export
Generate Private Key From Certificate Request Form

9. The certificate export wizard will start, please click Next to continue. In the next window select Yes, export the private key and click Next
10. Leave the default settings selected and click Next.
11. Set a password on the private key backup file and click Next
12. Click on Browse and select a location where you want to save the private key Backup file to and then click Next to continue. By default the file will be saved with a .pfx extension.
13. Click Finish, to complete the export process
3. Convert to RSA Private Key Format
The private key is backed up as a ‘.pfx’ file, which stands for Personal Information Exchange.
To convert it to RSA Private Key format supported by inSync:
1. Download and install latest version of OpenSSL for windows from http://www.slproweb.com/products/Win32OpenSSL.html.
Note: OpenSSL requires Visual C++ 2008 Redistributables which can be downloaded from the same website.
2. Open command prompt, navigate to C:OpenSSL-Win32bin>, and run the following commands.
3. The private key will be saved as ‘myserver.key’.
4. Carefully protect the private key. Be sure to backup the private key, as there is no means to recover it, should it be lost.
Purpose: Recovering a missing private key in IIS environment.
For Microsoft II8
(Jump to the solution)
Cause:
Entrust SSL certificates do not include a private key. The private key resides on the server that generated the Certificate Signing Request (CSR). When installed correctly, the Server Certificate will match up with the private key as displayed below:
If the private key is missing, the circled message indicating a good correspondence with private key will be missing as shown here:
A missing private key could mean:
- The certificate is not being installed on the same server that generated the CSR.
- The pending request was deleted from IIS.
- The certificate was installed through the Certificate Import Wizard rather than through IIS.
In this technote we do not discuss how to determine the reason the private key is missing. Select the link corresponding to each reason listed above for more information.
There's a video for this guide. Watch the video here.
1) Snap-In Configuration
2) Import the Server Certificate
3) Recover the private key
Use the following steps to add the Certificates snap-in:
1. Click Start, and then search for Run.2. Type in mmc and click OK.
3. From the File menu, choose Add/Remove Snap-in.
4. Select Certificates and then Add.
5. Choose the Computer account option and click Next.
6. Select Local Computer and then click Finish.
7. Click Close, and then click OK. The snap-in for Certificates (Local Computer) appears in the console.
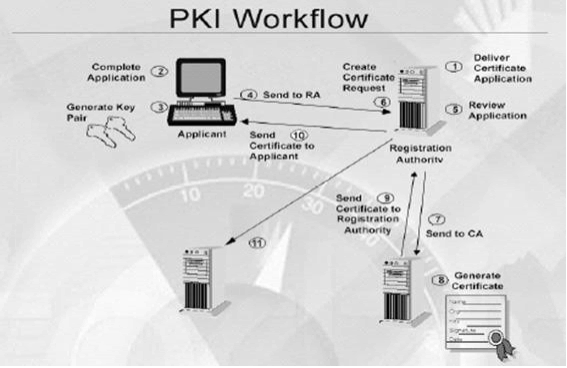 Use the following steps to import your Server Certificate into the Personal certificate store. If the Server Certificate has already been imported into the Personal store, you may skip this step.
Use the following steps to import your Server Certificate into the Personal certificate store. If the Server Certificate has already been imported into the Personal store, you may skip this step.From the MMC console opened in the above steps:
1. Expand the Certificates (Local Computer) tree in the left preview panel.
2. Right-click Personal and select All Tasks > Import.
3. The Certificate Import Wizard appears. Click Next.
4. Browse to the location of your Server Certificate file and click Next.
5. Select Place all certificates in the following store and click Next.
6. Click Finish to complete the Certificate Import Wizard.
7. A dialog box appears indicating the import was successful. Click OK.Use the following steps to recover your private key using the certutil command.
1. Locate your Server Certificate file by opening Microsoft Internet Information Services Manager, then on the right side select Tools > Internet Information Services (IIS) Manager.
2. Once in IIS Manager, select your server, then on the right side, Server Certificates. You will see all certificates currently on that server. Scroll over the certificate you are trying to install, right click, then select View.
3. There, you can view the certificate information. As you can see, there is no indication of a good correspondence with the private key.
4. Click the Details tab. Write down the serial number of the certificate.
5. We will need to recover the private key using a command prompt. In order to recover the key, we must do so using command prompt as an administrator. To do so, slick Start, then on then open all App. Under Windows System, find Command Prompt. Right click Command prompt and then Run as administrator. Confirm the action and continue.
6. Make sure you are on the right directory in command prompt.
e.g., if your server directory is “c:/users/srv2012_r2_std_x64”, on the command line type “cd c:/users/srv2012_r2_std_x64”. Note that “cd” is the command used to change directories in command prompt.
7. Now that we are in the right place, enter the following command at the prompt: certutil –repairstore my <serial number> where <serial number> is the serial number obtained in Step 2 with spaces removed.
8. If Windows is able to recover the private key, you see the message:
CertUtil: -repairstore command completed successfully.
If your private key was recovered successfully, your Server Certificate installation is complete.
If the private key was not recovered successfully, you will need to generate a new Certificate Signing Request and submit it to Entrust Datacard to have your certificate re-issued, or re-issue the certificate using your ECS Enterprise account.
Check that your Certificate has been successfully installed by testing it on the Entrust SSL Install Checker.
If you have any questions or concerns please contact the Entrust Certificate Services Supportdepartment for further assistance:
Hours of Operation:
Sunday 8:00 PM ET to Friday 8:00 PM ET
North America (toll free): 1-866-267-9297
Outside North America: 1-613-270-2680 (or see the list below)
Generate Private Key From Certificate Request Online
NOTE: It is very important that international callers dial the UITF format exactly as indicated. Do not dial an extra '1' before the '800' or your call will not be accepted as an UITF toll free call.
Windows Generate Certificate Request
Country | Number |
Australia | 0011 - 800-3687-7863 1-800-767-513 |
Austria | 00 - 800-3687-7863 |
Belgium | 00 - 800-3687-7863 |
Denmark | 00 - 800-3687-7863 |
Finland | 990 - 800-3687-7863 (Telecom Finland) |
France | 00 - 800-3687-7863 |
Germany | 00 - 800-3687-7863 |
Hong Kong | 001 - 800-3687-7863 (Voice) |
Ireland | 00 - 800-3687-7863 |
Israel | 014 - 800-3687-7863 |
Italy | 00 - 800-3687-7863 |
Japan | 001 - 800-3687-7863 (KDD) |
Korea | 001 - 800-3687-7863 (Korea Telecom) |
Malaysia | 00 - 800-3687-7863 |
Netherlands | 00 - 800-3687-7863 |
New Zealand | 00 - 800-3687-7863 0800-4413101 |
Norway | 00 - 800-3687-7863 |
Singapore | 001 - 800-3687-7863 |
Spain | 00 - 800-3687-7863 |
Sweden | 00 - 800-3687-7863 (Telia) |
Switzerland | 00 - 800-3687-7863 |
Taiwan | 00 - 800-3687-7863 |
United Kingdom | 00 - 800-3687-7863 |